MANAGED SERVICES 1STAFF POWERED BY MICROSOFT
Vulnerability scanning and penetration testing are two imperative techniques for mitigating cyber risks. They are very different, yet many business owners often get confused by them, and some take more importance on one over the other.
Let us break it down to clarify the differences between vulnerability scanning and penetration testing.
What is vulnerability scanning?
Vulnerability scanning aims to discover weaknesses in your IT environment, from firewalls, software, web applications, and servers, to devices connecting to your network. It typically uses an automated tool with minimal assistance from trained cybersecurity professionals and generates a report of your vulnerabilities, highlighting those that pose the greatest risk to your organization.
Vulnerability scanning is vital to help your business:
- Detect where the vulnerabilities lie in your system.
- Take necessary steps to fix those vulnerabilities to better protect against cyber-attacks.
- Achieve data protection and security regulations compliance relevant to your industry.
- Proactively protect your business data against cyber threats.
What is penetration testing?
Unlike vulnerability testing, which only tells you your IT environment’s weaknesses, penetration testing (or pen test) goes the extra mile. It attempts to see if you can really do something negative about the vulnerabilities in your network, applications, servers, and devices by simulating an attack. It is usually done by highly skilled security analysts and ethical hackers, finding ways to hack into your system and determine how much damage could be done.
Penetration testing is essential to your business to help you:
- Test the overall health of your apps, network, and devices.
- Expose IT systems most susceptible to a cyber-attack.
- Reinforce your security posture by addressing specific vulnerabilities.
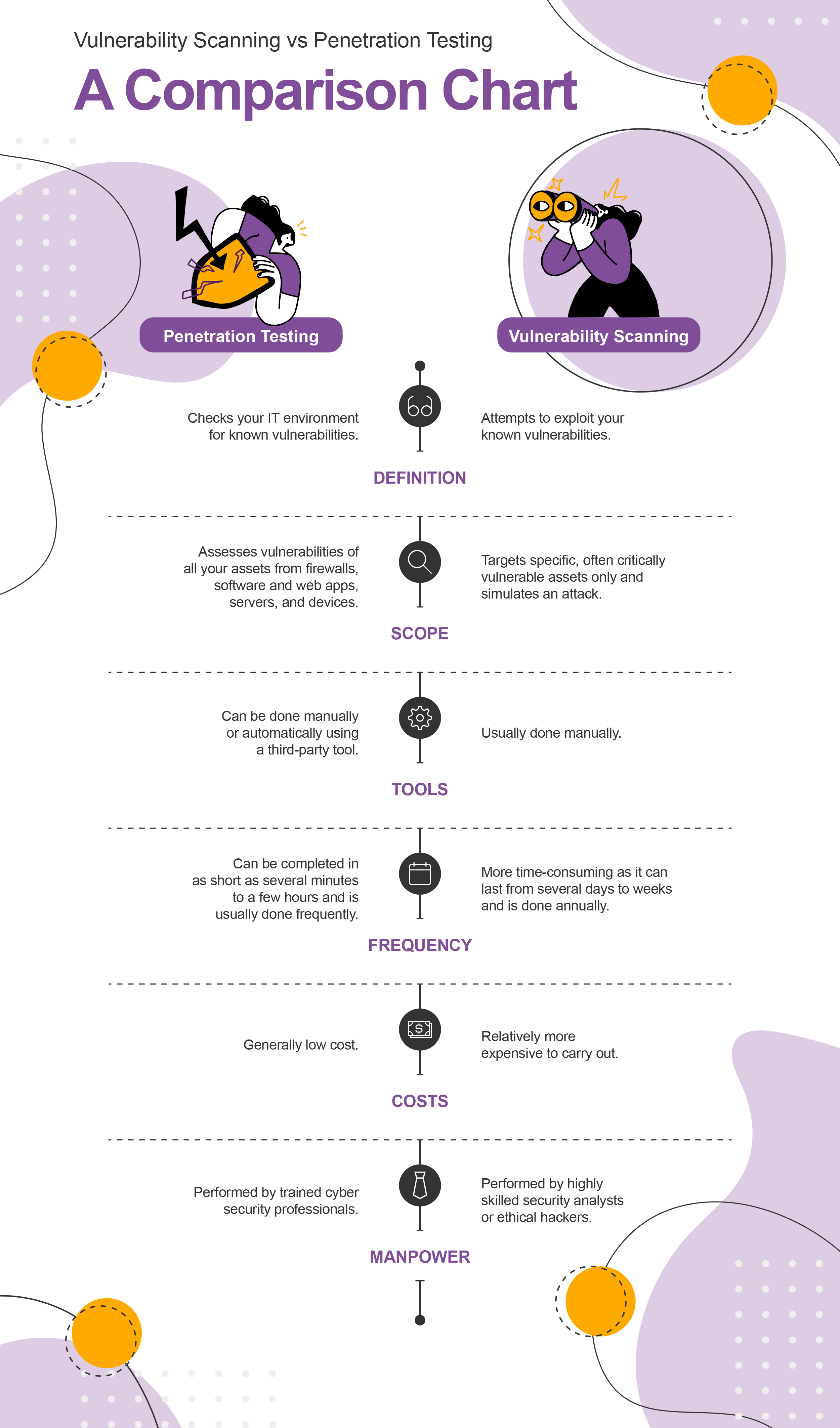
Which is better – vulnerability scanning or penetration testing?
Both vulnerability scanning and penetration testing play an important role in cybercrime prevention. Whilst vulnerability scanning is a good starting point to surface your IT environment’s weaknesses, penetration testing provides you with a clearer understanding of the severity of your vulnerabilities. Both are robust methods to monitor and improve your business’ cyber security and are highly recommended to be part of every organization’s IT strategy.
Download your copy of the vulnerability scanning vs penetration testing comparison chart.

More from the blog
Should you choose a Best-of-Breed or All-in-One Security Solution?
If we were in the 1990s, a best-of-breed strategy would likely prevail and win this debate (for reasons you can read through in this blog). But in today’s modern workplaces with hybrid workstyles, cloud-based technologies, bring your own device (BYOD), the Internet of Things (IoT), artificial intelligence (AI), machine learning (ML), and a whole bunch of other new tech, it has completely changed the way organizations need to manage, administer, and protect their IT environment.
Read more...